2 minutes
NahamCon CTF 2024 - Buggy Jumper 1 [EN]
| Catégorie | Mobile |
| Difficulté | Easy |
| Auteur | matlac |
Introduction
Buggy Jumper is a new mobile game that can be enjoyable for both gamers and hackers! There's a lot going on, can you get some of game's source code to see whats happening behind the scenes?
Decompilation
Let’s start the challenge by decompiling the mobile application with jadx.
We got the following file structure :
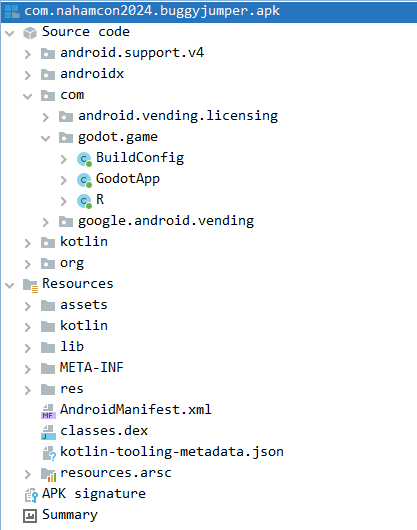
The AndroidManifest.xml file provides essential information about an Android application, including its components (activities, services, broadcast receivers), permissions, hardware and software features required, and the application’s entry point (MainActivity). The MainActivity is the primary activity that is launched when the user starts the application. :
<activity android:theme="@style/GodotAppSplashTheme" android:label="@string/godot_project_name_string" android:name="com.godot.game.GodotApp" android:exported="true" android:excludeFromRecents="false" android:launchMode="singleTask" android:screenOrientation="portrait" android:configChanges="density|smallestScreenSize|screenSize|uiMode|screenLayout|orientation|navigation|keyboardHidden|keyboard" android:resizeableActivity="true">
<meta-data android:name="com.oculus.vr.focusaware" android:value="true"/>
<intent-filter>
<action android:name="android.intent.action.MAIN"/>
<category android:name="android.intent.category.LAUNCHER"/>
<category android:name="com.oculus.intent.category.VR"/>
</intent-filter>
</activity>
With jadx, we can view the code of the main activity com.godot.game.GodotApp
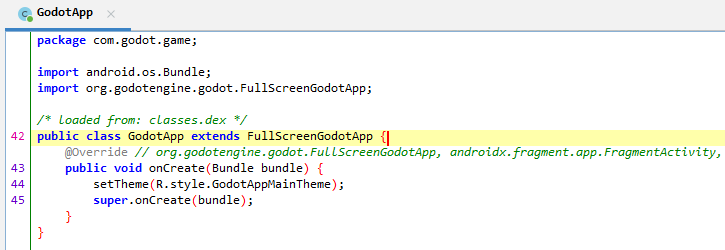
There is no interesting information in the main activity, but we quickly understand that it is an application developed in Go. By digging through the sources, we can find multiple files written in Go.
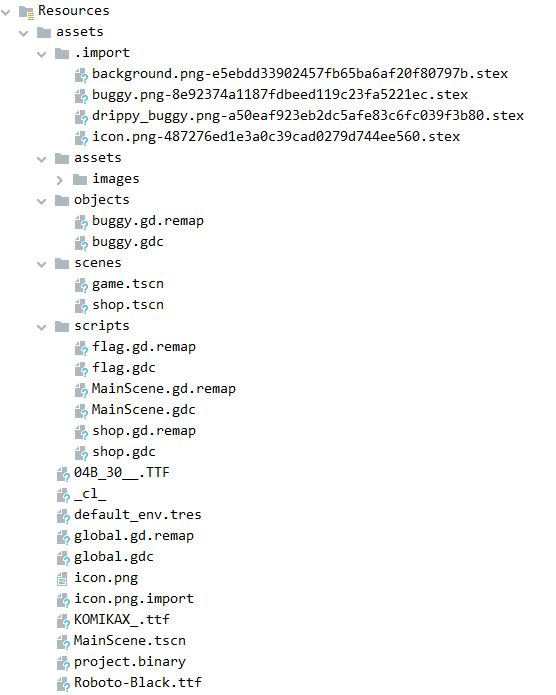
We can see the file flag.gdc compiled in Go
We can use a Go decompiler to obtain the source code of the files. We’ll use gdsdecomp We will be able to retrieve the Go source files:
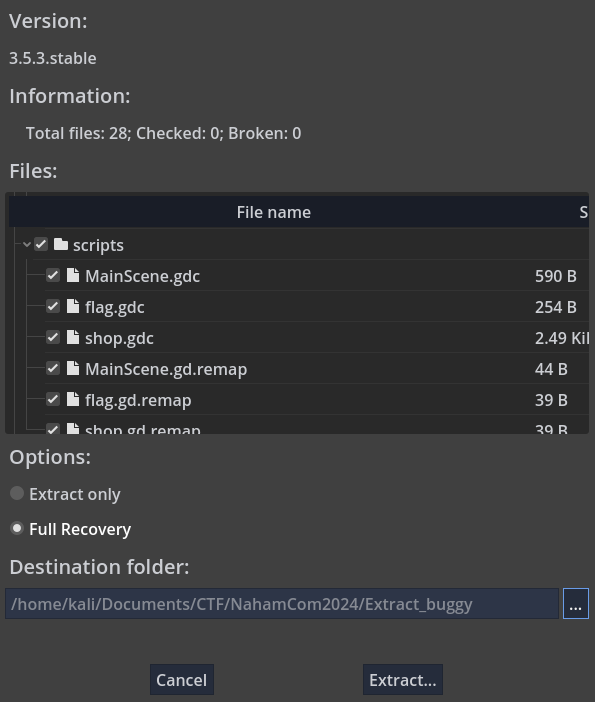
We have successfully extracted the Go files from the application
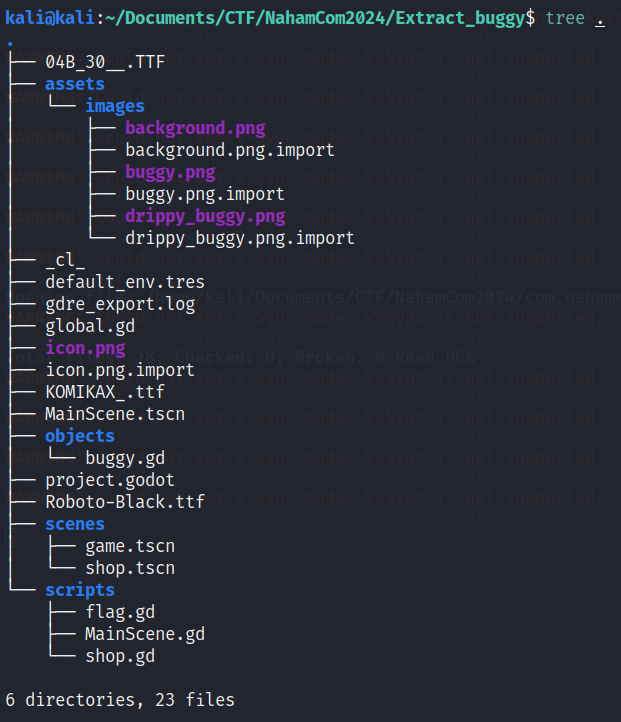
We can look through the uncompiled flag.gd file.